THM | Pickle Rick🥒
I turned myself into a pickle, Morty!!
Welcome to my writeup for the PickleRick CTF, which was my first ever CTF on TryHackMe... This challenge walks you through web enumeration, command injection, and privilege escalation in a quirky, story-driven setting.
1. Scanning (Nmap)
As with any good CTF, the first step is to map out the target. I started with a basic Nmap scan against the IP 10.10.40.167 to discover open ports and running services: (your ip might be different)
nmap -sC -sV 10.10.40.167
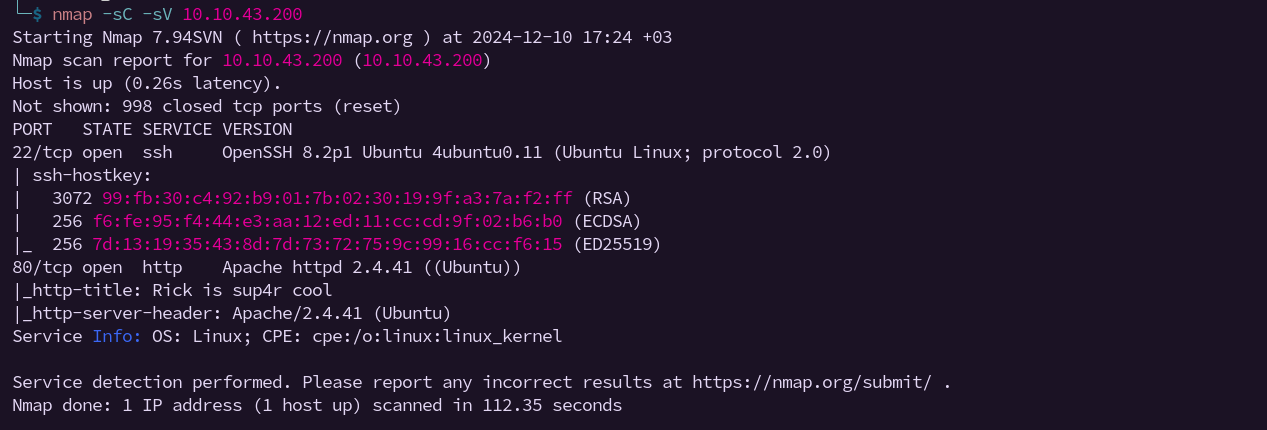
Scan Findings:
- Port 22 (SSH): Likely safe for now unless we get credentials.
- Port 80 (HTTP): Our gateway to the challenge.
2. Exploring the Web Service
Navigating to (http://10.10.40.167) reveals a web page begging for our help—Rick is in trouble!
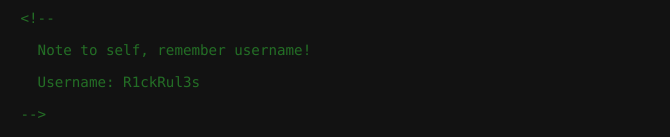
A quick view of the page source uncovers a hidden username: R1ckRul3s.
Next, I used gobuster to enumerate hidden directories and files on the web server:
gobuster dir -u http://10.10.40.167 -w /usr/share/dirb/wordlists/common.txt
Notable discoveries included:
- robots.txt – Often a goldmine for hints.
- login.php – A login portal that looked promising.
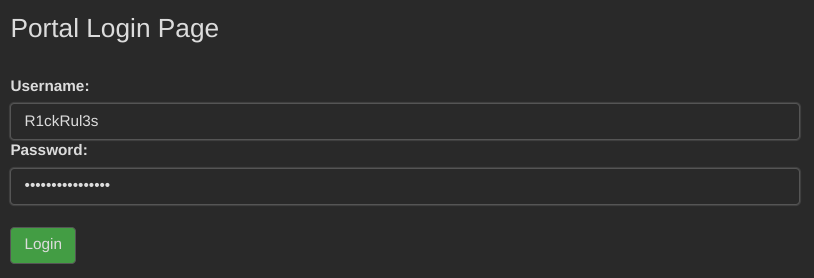
2. Getting Authenticated
Browsing to login.php, I used the previously spotted username. Checking robots.txt yielded what appeared to be a BURRRP-- password. Logging in with these credentials granted access to a command portal—Rick’s secret command center!
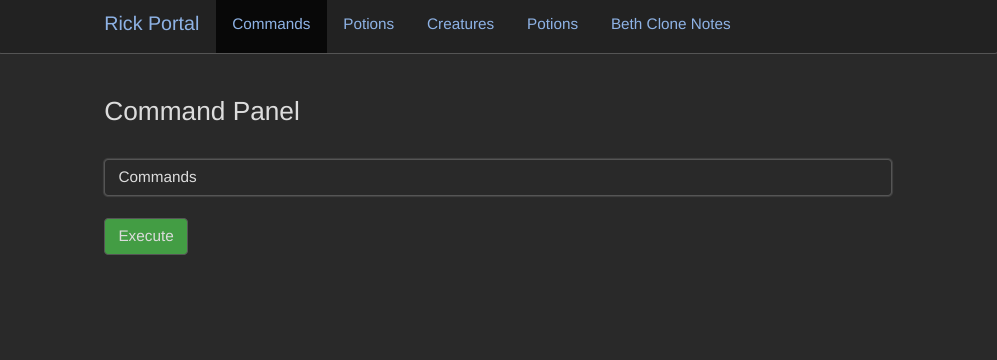
4. Command Portal
Once inside the command portal, a quick ls revealed several files:
- Sup3rS3cretPickl3Ingred.txt
- clue.txt
Trying to read the secret ingredient using cat wasn’t an option (the command was disabled!).
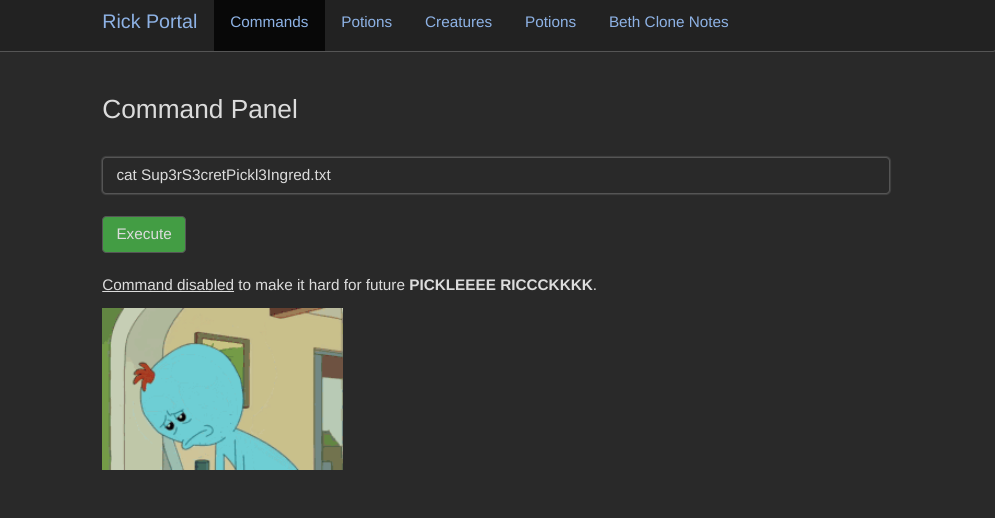
I tried the less command to view the file.
less Sup3rS3cretPickl3Ingred.txt
The contents of Sup3rS3cretPickl3Ingred.txt provided the first ingredient for Rick’s transformation. I then inspected clue.txt, which hinted at the location of the remaining ingredients.
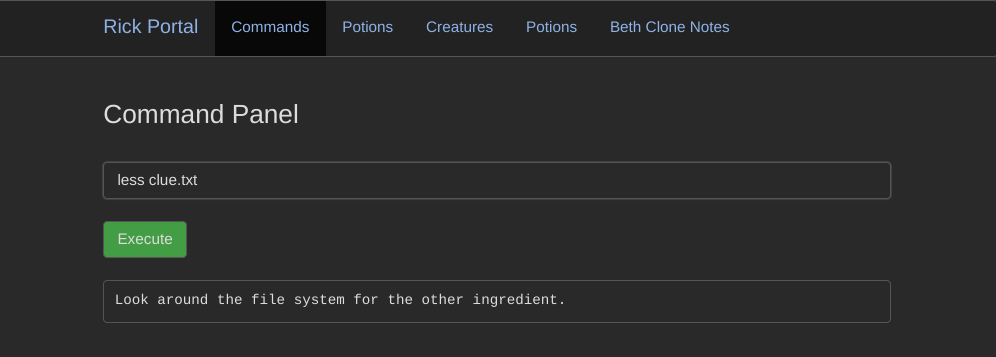
less "/home/rick/second ingredients"
A. Third Ingredient – privilege escalation
The final ingredient was in the /root directory. However, as the www-data user, I couldn’t access /root directly. Running:
ls /root
returned permission denied. Time for privilege escalation!
Elevating Privileges
Checking for sudo privileges with:
sudo -l
The output revealed that all commands could be run as root without requiring a password:
This is a critical misconfiguration in the sudoers file. It means that the www-data user can execute any command with root privileges without needing a password, effectively allowing full system takeover. In real-world scenarios, this level of privilege escalation could lead to complete system compromise.
To exploit this, I listed the contents of /root and retrieved the final ingredient:
sudo ls /root
Then, using less, I read the final ingredient file:
sudo less /root/3rd.txt
Why is this a vulnerability?
Normally, only trusted users should have sudo access to root commands. The NOPASSWD: ALL setting in /etc/sudoers allows any command to be run without authentication, making it easy for an attacker to escalate privileges.
A safer configuration would be to limit sudo access to only necessary commands instead of granting full root privileges.
Wrapping Up
And that’s it! 🎉 We successfully completed the PickleRick challenge, and I hope you enjoyed reading through my writeup and learned something new.
Feel free to reach out if you have any questions or thoughts about this writeup. I’d love to hear your experiences or any tips you may have. Until next time, stay curious and keep hacking!